Depending on the level of security you wish, learning how to block a website may require a adjustments of your web browser, the use of internet filtering software or editing of your host file. At any rate you can try all methods to see which works best for you.
Block a Website using Internet Explorer:
Internet Explorer version 5 and later offer the ability for heighten security and privacy. You can block a site by following the directions below:
- Load your Internet explorer
- Click Tools
- Click Internet Options
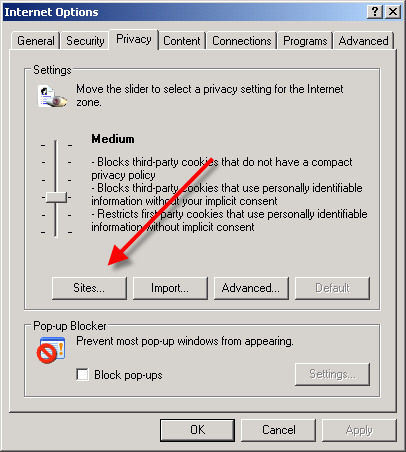
- Click the Privacy tab
- Under the Privacy window, Click Sites
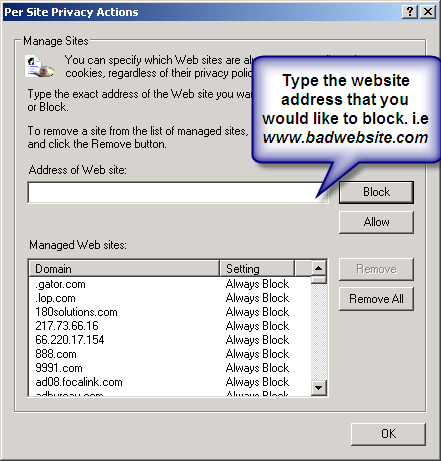
- Type in the site address that you want to Block and Click OK.
Other way to block a website using Internet Explorer:
Click Tools ->Internet Options->Security->Restricted sites->Sites->Type in the site address and Click ADD then click OK.
Block A Website in All Web Browsers:
This action will require you to edit your Host file. Your host file is a computer file used to store information on where to find a node on a computer network.
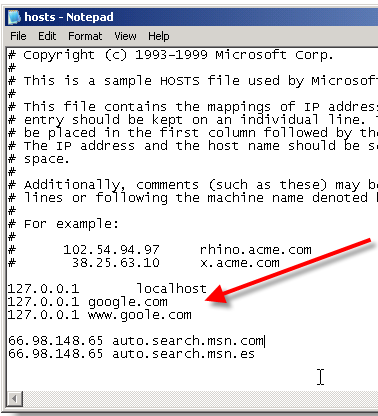
Here are the steps in Windows XP:
- Click Start->All Programs->Accessories->Command Prompt2.
- Click Command Prompt This will open a DOS command window.
- Type: notepad C:/Windows/System32/drivers/etc/hosts
- Locate the line 127.0.0.1 localhost
- To block the website google.com for example, just add this text under 127.0.0.1 localhost:
127.0.0.1 google.com
127.0.0.1 www.google.com
- You can add as many sites any site, However you will need to prefix it with "127.0.0.1".
- Save the file